Problem
WMI-based connectors may not activate, as their queries fail with a result of “WMI unavailable (Access denied )”. This occurs because some antivirus products (notably F-Secure) block access to the required WMI namespace.
Example
In particular this behavior has been observed on IBM xSeries systems equipped with ServeRAID controllers. The connector used to monitor these RAID controllers is SMI-S Compliant RAID Controller - Windows.
The relevant information is in the “root\LSI_MR_1_3_0” namespace, however the antivirus product creates its own namespace (root\FSECURE), which blocks queries to all namespaces listed after it.
Resolution
The resolution to this problem is to add a configuration variable forcing the use of the correct WMI namespace.
In TrueSight:
- Edit the CMA policy.
- In the List of Devices, select the Edit option for the appropriate device.
- Scroll to the bottom of the resulting window, and next to Device Additional Configuration Variables, click Add. This will add a device-specific configuration variable.
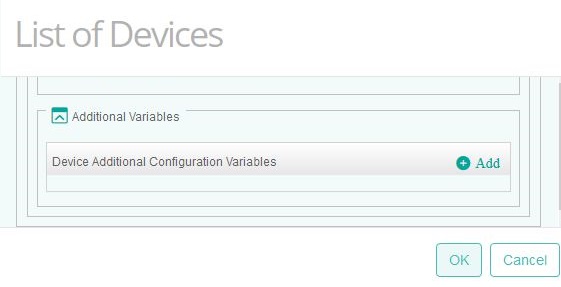
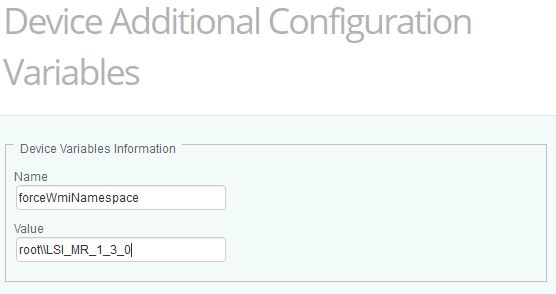
- Specify a new variable with the Name :
forceWmiNamespaceand the Value of the required namespace (in our example,root\\LSI_MR_1_3_0).
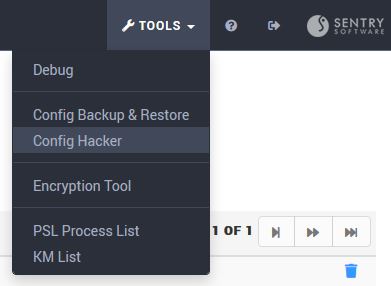
In Monitoring Studio X UI
- In the Monitoring Studio X UI, click on TOOLS, and from the menu, select Config Hacker.
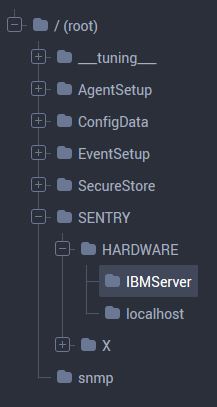
 2. From the tree on the left, navigate to
2. From the tree on the left, navigate to SENTRY > HARDWARE > DeviceID, where DeviceID is the Device ID of the remote system being monitored.
- Click the ADD VARIABLE button.
- Specify the variable, with a Path of
/SENTRY/HARDWARE/<DeviceID>/forceWmiNamespace, and the Value of the required namespace (in our example,root\LSI_MR_1_3_0).
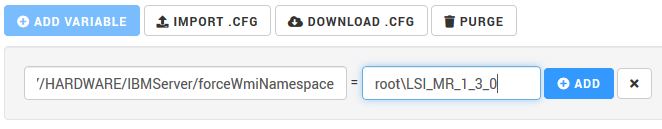
- Click the ADD button, to apply the new variable.
