Problem
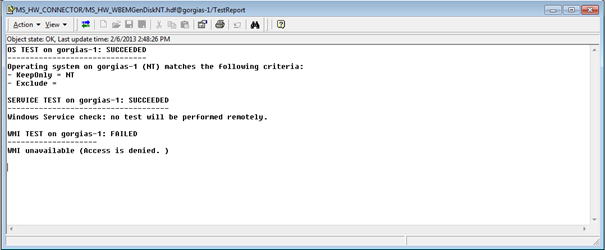
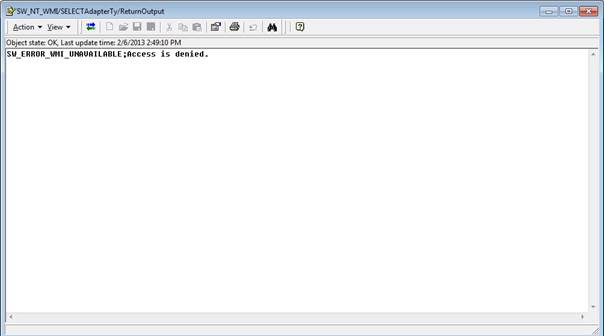
Remote Windows 2008 servers cannot be monitored using WMI and local admin accounts, even though they belong to the Administrators group. An "Access is denied" error message is usually returned. This error occurs when the User Account Control (UAC) is enabled on the Windows 2008 servers because UAC affects the WMI data that is returned from a command-line tool, remote access, and how scripts must run (see User Account Control and WMI).
The Sentry Software’s products affected by this issue are:
- Hardware Sentry KM for PATROL
- Monitoring Studio KM for PATROL
Issue Reproduction Steps
Hardware Sentry KM for PATROL
In Hardware Sentry KM for PATROL, the issue occurs under the following circumstances:
- Right-click the KM Main Icon > Remote Add a Remote System or an External Device
- Accept the End User License Agreement and click Next.

- Enter the Name and IP Address of the Windows 2008 server to be monitored, select Microsoft Windows, and click Next
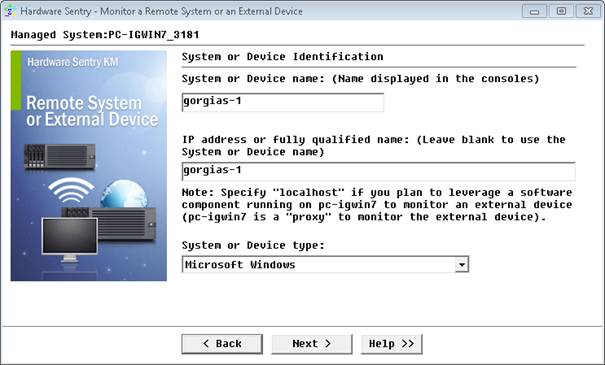
- Select Manually choose which connectors to use and click Next.
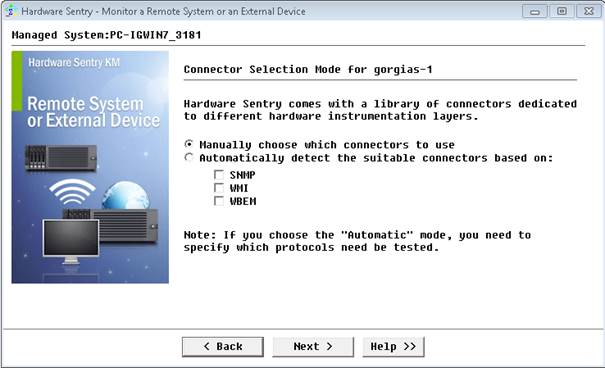
- Select one or several WMI-based connectors (WMI - Battery, WMI - Disks, WMI - HBA, WMI - Network) and click Next.
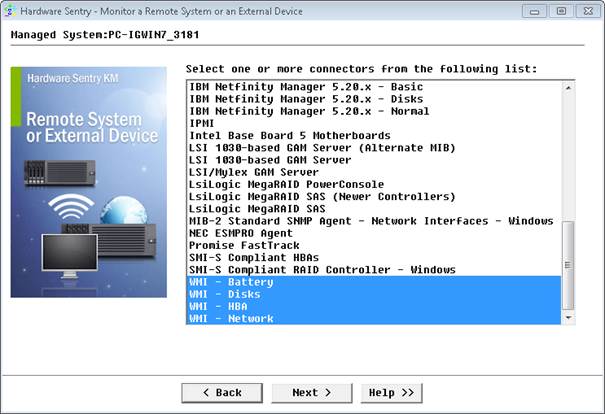
- Use a local admin account (in our example gorgias-1\patrol) and click Next.

- Click Finish. The error message is then displayed in the TestReport text parameter of the connector.
Monitoring Studio KM for PATROL
In Monitoring Studio KM for PATROL, the issue occurs under the following circumstances:
- Right-click the Application Container main icon > KM Commands > New > WMI Query Analysis and click Next.
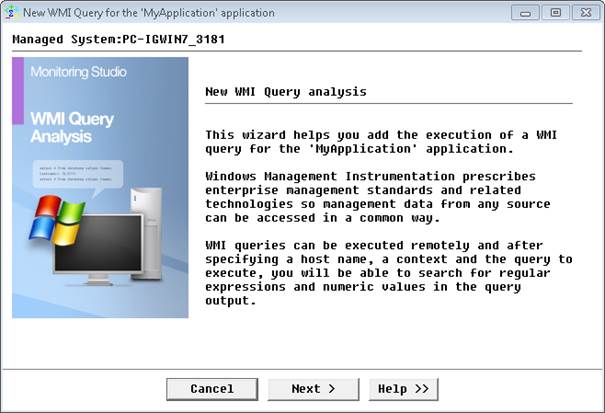
- Specify the Windows 2008 Server to be monitored (e.g.: GORGIAS-1), the WMI Query to be run, the local admin account to be used (e.g.: gorgias-1\patrol) and click Next.
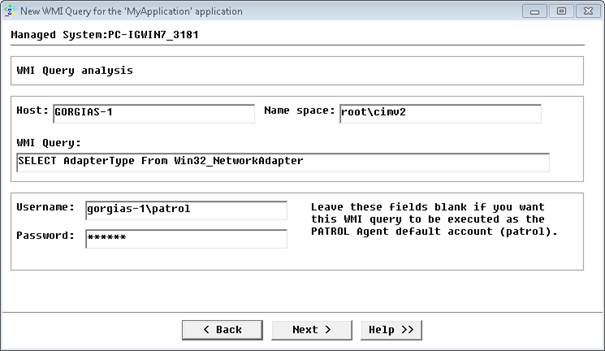
- Click Finish. The error message is then displayed in the ReturnOutput text parameter.
Solution
To solve this issue you can either:
- Use a domain account (<yourdomain>\<username>) and make sure that this account or the domain group it belongs to is part of the local administrators group of the monitored machine. You can also use the default built-in administrator account (Administrator)
- Or disable remote UAC:
- Under HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\system, create a new DWORD entry called LocalAccountTokenFilterPolicy
- Set its value to 1.

You should now be able to monitor Windows 2008 servers with WMI and a local account.
Related Topics
- Troubleshooting WMI-Based Connectors
- Troubleshooting the Monitoring of Fiber Channel Cards on Windows Systems
- Unable to Perform Remote Monitoring from Windows 2008 Servers with UAC Turned on
- Unable to Monitor Hardware Using SNMP-based Connectors with PATROL Agent v.9.5.00.02
- Enabling Debug from the Command-line Interface
