Introduction
This article explains the pre-requisites and procedure involved in monitoring a server installed with VMware ESX/ESXi.
All versions of ESX/ESXi are monitored remotely, using WBEM Credentials to connect to the VMWare Host.
Prerequisites
PATROL/TrueSight/Hardware Sentry
The PATROL Agent and Hardware Sentry needs to be installed on a remote machine. This machine can be another server or a virtual machine on the VMware ESX Server.
ESX WBEM Credentials
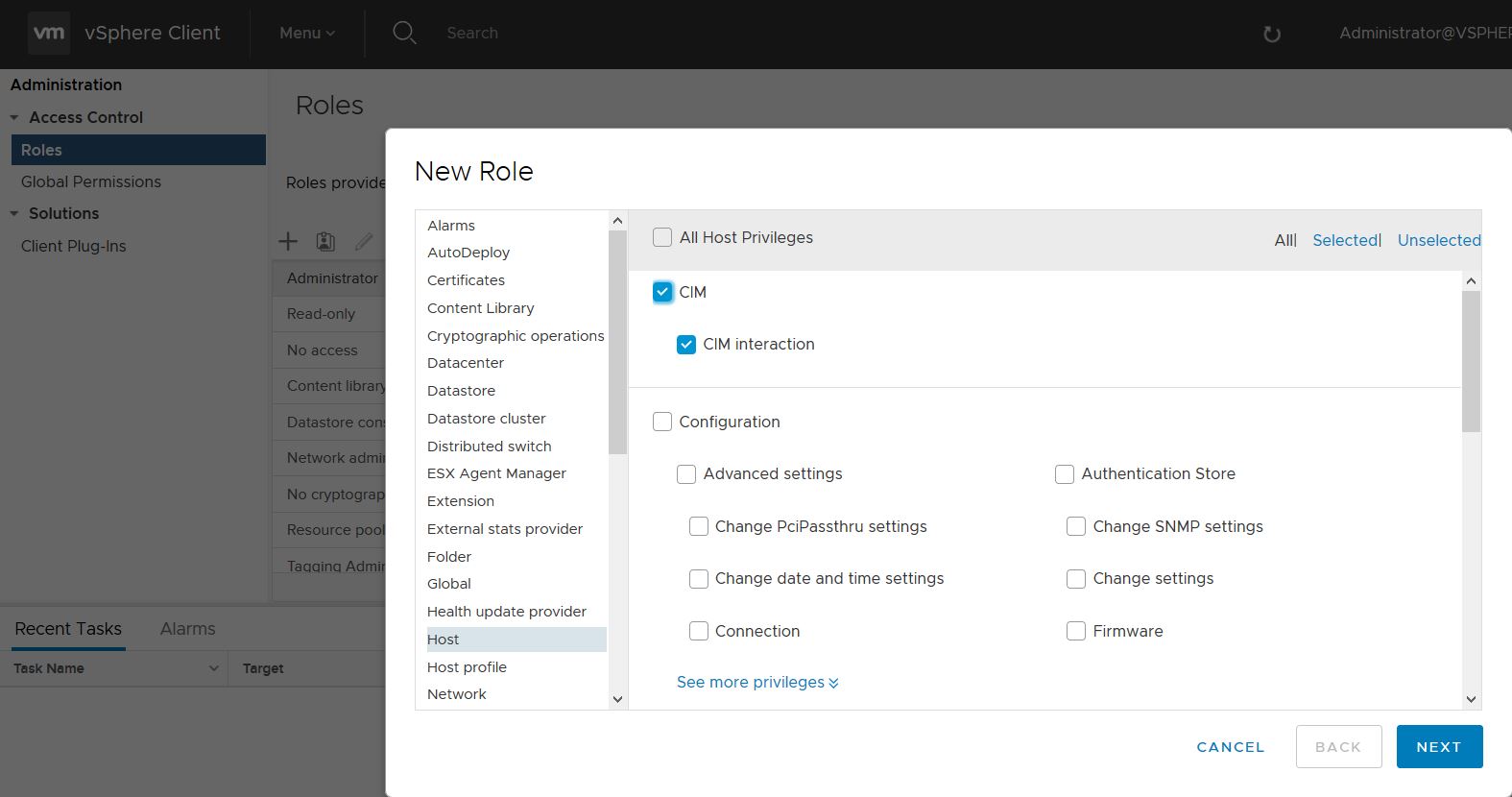
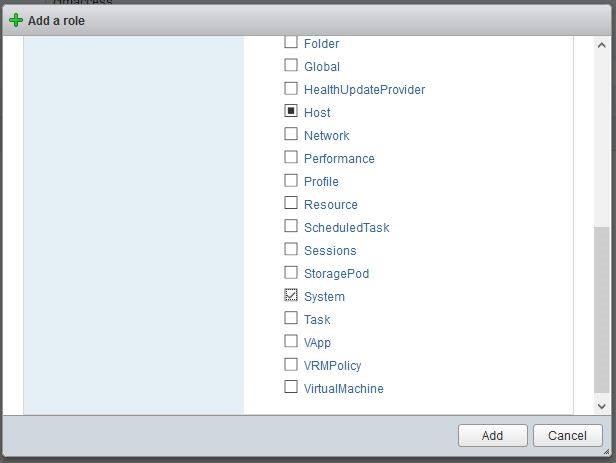
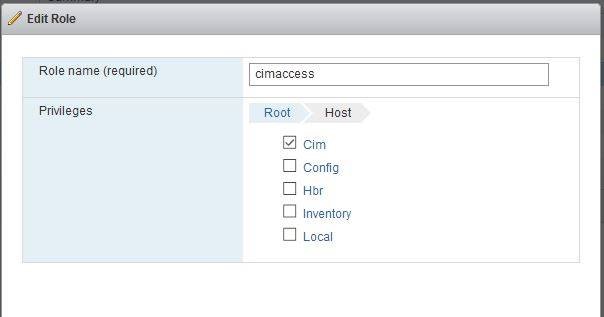
The WBEM Credentials specified should be server level vSphere / vCenter passwords. The minimum rights required for the user’s role are All Privileges / Host / CIM / CIM Interaction.
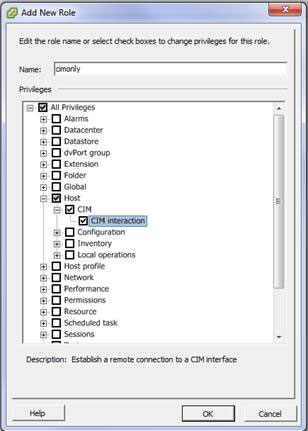
The role privileges can be found:
- in Menu > Administration > Access Control > Roles in vCenter:
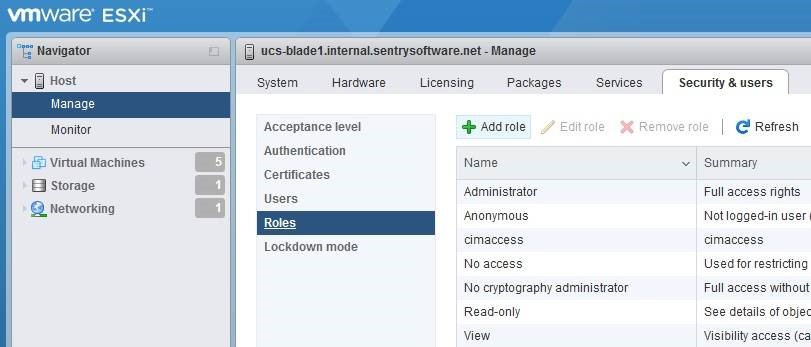
- in Host > Manage > Security & Users > Roles in the ESXi Web Client. In this case, System privileges should also be selected:
Procedure
For PATROL
To monitor VMware ESX/ESXi servers:
-
In the PATROL Console, right-click on the main Hardware icon > KM Commands > Add a Remote System or External Device.
-
Provide an Internal ID for the system, and enter the Hostname of the VMware ESX host (not one of the virtual machines).
-
From the Device Type drop-down list, select Management Card/Chip, Blade Chassis, ESXi and click Next.
-
Select the WBEM protocol and click Next.
-
Select Manually choose which connectors to use and click Next.
-
Select VMWare ESXi 4.x (ESX4/5/6) or VMWare ESXi 3.x (ESX3i), VMware ESXi - Disks connectors. If the server has an HBA, select SMI-S Compliant HBAs as well. Click Next.
-
Configure the WBEM connection settings:
- Set the Port to 5989 and check Encrypt Data.
- Specify valid vSphere/vCenter credentials for the host.
- Click Next.
-
Click Next, then Finish.
For TrueSight
- Create a policy or edit an existing policy.
- In the Hardware Configuration section, locate List of Devices and click Add to add a new device to your monitoring environment.
- Specify an Internal ID and the Hostname or IP address of the ESXi host.
- From the Device Type drop-down list, select Management Card/Chip, Blade Chassis, ESXi.
- In the Protocol/Connection Information section:
- Expand WBEM, and check the Enable WBEM box
- Specify valid vSphere/vCenter credentials for the host
- Ensure that Port is set to 5989, and Encryption is enabled.
- Click OK twice.
- Save the Monitoring Policy.
Known Issues
Non-Certified Components
Generally only VMWare certified (HCL) servers / components will work with the VMware ESXi/ESX4i connectors. Components / Sensors that are not listed in the VMWare management consoles (vSphere, etc..) will not be discovered / monitored.
The QLogic / Emulex SMI-S proxies included with VMware ESX4 often return a status of “Unknown” for HBAs / Logical Disks located on a SAN. It is thus not possible to collect a valid status for these HBAs / Logical Disks.
Root Permissions Required
ESXi versions 4.1 to 5.5 have a known issue that prevents any user not part of the “root” group from accessing the CIMserver. A workaround to this is to create a separate user that is part of the root group, but that has no access rights.
-
Create a user, add it to the root group:
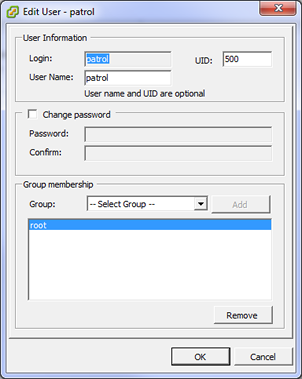
Note: From ESXi v.5.1 and higher, groups are no longer available in the vSphere GUI. To work around this specific problem, please use telnet/ssh to connect to the ESX and manually edit the /etc/group file and add that user to the “root” group as follows:
~ # vi /etc/group
root:x:0:root,patrol
daemon:x:2:daemon
users:x:100:
nfsnobody:x:65534:
users:x:100:vpxuser
patrol:x:1000:
You could also use vCenter central authentication, and this feature is available starting from version 1.8.01 of the Hardware Sentry KM.
- In Permissions for the esx host, set this user’s role to No Access:
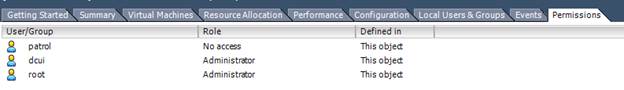
- The user will now be able to access the cimserver to collect component status, but not to anything else:
ESXi 7 Permissions
With ESXi v7.xx, if you update the /etc/group file, your changes will be lost after the ESXi server restarts. This is a known VMWare issue.
As a result, you must use either a local account with Administrator role at the ESXi level,
or use an account with the “CIM interaction” privilege, defined at the vCenter level.