Description
How to optimize the use of the 'sudo' utility with Hardware Sentry KM for PATROL.
Solution
The need for root privileges
On Linux and UNIX systems, gathering the status of hardware devices sometimes requires running commands with root privileges. In such cases, Hardware Sentry KM can be configured to impersonate as root to run these commands, but this will require configuring the KM with the root login and password, which many system administrators are reluctant to do for various reasons.
Alternately, Hardware Sentry KM can use the ‘sudo’ command line utility to run such commands with elevated privileges without entering the actual root password.
Note: This article also applies to equivalents of the 'sudo' command line utility that provide the same impersonation mechanisms. This article explains how to configure Hardware Sentry KM to use ‘sudo’ when root privileges are required.
Prerequisites
System administrators must have properly configured the ‘sudo’ utility and its /etc/sudoers configuration file to allow the PATROL Agent’s default account to impersonate as root without requiring to type in a password.
Configure the KM to use ‘sudo’ (through the PATROL Console GUI)
In the PATROL Console (both PATROL Central and PATROL Classic Console), you can select the commands that Hardware Sentry KM will execute through ‘sudo’:
- Right-click the main Hardware Sentry KM icon › KM Commands › This System’s Settings › Connection, Credentials and Connectors…
- In the dialog box, click the Sudo options button.
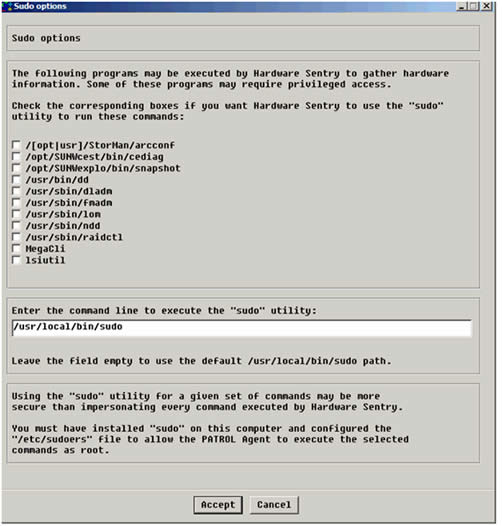
- The selected will be added to the /SENTRY/HARDWARE/useSudoCommandList variable in the PATROL Agent configuration and will be executed with the 'sudo' utility. You can also specify the path (and optionally arguments) to the ‘sudo’ command.
Note: Only the commands relative to the connectors you have chosen will be shown in the configuration wizard.
Configure the KM to use ‘sudo’ (directly in the agent’s configuration)
Whether and how the KM will use 'sudo' to execute commands is stored in variables in the PATROL Agent’s configuration under /SENTRY/HARDWARE/localhost:
| Variable | Description |
sudoCommand |
Syntax of the 'sudo' command (including its full path and optional arguments) that will be used by Hardware Sentry to launch the external commands specified in the useSudoCommandList variable. |
useSudoCommandList |
Line-separated list of commands that will be launched by Hardware Sentry through the ‘sudo’ utility. |
Example:
/SENTRY/HARDWARE/localhost/sudoCommand=/usr/local/bin/sudo
/SENTRY/HARDWARE/localhost/useSudoCommandList=/opt/SUNWcest/bin/cediag
The list of commands in the useSudoCommandList variable must match exactly how the KM executes these commands (including the path to the executable). Please refer to the table below to see which commands can be specified in the useSudoCommandList variable depending on the connectors being used to monitor the system.
| Connector | Hardware KM Sudo Variable (Not used in PM) |
Commands run using sudo |
| MS_HW_AdptStorManUnix.hdf | /[opt|usr]/StorMan/arcconf | /opt/StorMan/arcconf getversion /opt/StorMan/arcconf getconfig /usr/ StorMan/arcconf getversion /usr/ StorMan/arcconf getconfig |
| MS_HW_Director4Linux.hdf | /opt/IBM/director/CIMOM/bin/cimcli | /opt/IBM/director/CIMOM/bin/cimcli |
| MS_HW_HPUX.hdf | /usr/bin/adb | /usr/bin/adb /stand/vmunix /dev/kmem /usr/bin/adb -k /stand/vmunix /dev/kmem |
| MS_HW_HPUXDisk.hdf | /usr/sbin/diskinfo | /usr/sbin/diskinfo $deviceID |
| MS_HW_HPUXSasMgr.hdf | /opt/sas/bin/sasmgr | /opt/sas/bin/sasmgr get_info -D $deviceID |
| MS_HW_HPUXSAUtil.hdf | /opt/raidsa/bin/sautil | /opt/raidsa/bin/sautil $volumeID |
| MS_HW_IBMAIXChrpMachstat.hdf | /usr/sbin/bootinfo /usr/sbin/machstat |
/usr/sbin/bootinfo -p /usr/sbin/machstat -f |
| MS_HW_IBMAIXDisk.hdf | /usr/bin/dd | /usr/bin/dd if=/dev/r$1 of=/dev/null count=20 2›&1 |
| MS_HW_IpmiTool.hdf | ipmitool | Various commands are run. |
| MS_HW_LinuxNetwork.hdf | ethtool | /usr/sbin/ethtool $deviceID |
| MS_HW_LSIUtilUNIX.hdf | lsiutil | lsiutil -p $controllerID -a 1,2,0 21 |
| MS_HW_SmartMonLinux.hdf | /usr/sbin/smartctl /bin/dd |
/usr/sbin/smartctl -q onecheck /usr/sbin/smartctl -H /usr/sbin/smartctl /usr/sbin/smartctl -a $deviceID /usr/sbin/smartd /bin/dd if=$deviceID of=/dev/null count=20 2›&1 |
| MS_HW_SunCediag.hdf | /opt/SUNWcest/bin/cediag | /opt/SUNWcest/bin/cediag /opt/SUNWcest/bin/cestat |
| MS_HW_SunFmadm.hdf | /usr/sbin/fmadm | /usr/sbin/fmadm faulty /usr/sbin/fmadm config |
| MS_HW_SunIostat.hdf | /usr/bin/dd | /bin/dd if=$deviceID of=/dev/null count=20 2›&1 |
| MS_HW_SunIostatNonSun.hdf | /usr/bin/dd | /bin/dd if=$deviceID of=/dev/null count=20 2›&1 |
| MS_HW_SunMegaCli.hdf | MegaCli | MegaCli -AdpAllInfo -aALL -NoLog MegaCli -PDList -aALL -NoLog MegaCli -AdpBbuCmd -aALL -NoLog MegaCli -LDInfo -Lall -aALL -NoLog |
| MS_HW_SunNetwork.hdf | /usr/sbin/ndd /usr/sbin/dladm |
/usr/sbin/ndd $deviceID link_status /usr/sbin/ndd $deviceID link_speed /usr/sbin/ndd $deviceID link_mode /usr/sbin/ndd $deviceID link_duplex /usr/sbin/dladm show-dev |
| MS_HW_SunPrtdiag.hdf | /usr/sbin/lom | /usr/sbin/lom |
| MS_HW_SunRaidctl.hdf | /usr/sbin/raidctl | /usr/sbin/raidctl -S /usr/sbin/raidctl -l |
| MS_HW_SunScSnapshot.hdf | opt/SUNWexplo/bin/snapshot | /opt/SUNWexplo/bin/snapshot -c |
The list of commands that require root privileges is also listed in the Reference Guide (see the Connectors section). Otherwise, the list is provided in the GUI of the KM (see previous paragraph).
Related Topics
- How to Know Which Version of the Hardware Sentry KM is Currently Installed on Your System?
- Monitoring Cisco MDS 9000 Series FC Switches with Hardware Sentry
- Monitoring HP StorageWorks MSA2000/P2000 with Hardware Sentry
- Hardware Monitoring: Disabling Missing Device Detection
- Hardware Monitoring: Enabling Missing Device Detection
